It may be wrong to start with a topic that’s seldom under the cybersecurity team – but having a sensible naming convention is #1 on our list. A naming standard should allow you to tell different categories of devices apart and ideally indicate what part of the network it belongs to.
If it’s a mobile device, that would be the primary location. If it’s a static device, it would be nice to know the type of network it serves. Servers are often connected to one or more admin segments, but we’re looking for the network it uses to serve its purpose.
Next up is the inventory itself. And unless your asset management practice is truly world-class (it’s often not), we recommend that cybersecurity maintain their own inventory as much as possible. Cross-checking data between various data sources is truly a thing of beauty.
Any usable inventory is built on a working understanding of the network, i.e. a network overview presenting subnets. Everything else falls apart if we don’t know which subnets we’re working with, which are DMZ, which are server LANs, which are client LANs etc.
The cybersecurity inventory is best composed of two types of data:
On a side note, it’s not always possible or even a good idea to perform sweeping scans, but there are other options available, for example, passive sensors.
On the topic of data from specialized inventories, here is a golden opportunity to measure the quality of our inventory: the CMDB confidence score.
CMDB confidence score is a simple calculation that compares inventories that basically tells us the same thing, and compares how much they agree.
Consider a simple example below.
We have identified five inventories that tell us the number of Windows servers:
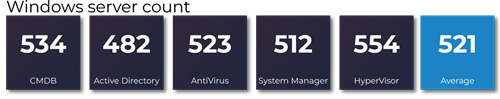
The numbers vary between 482 in Active Directory and 554 in the HyperVisor.
CMDB confidence calculation:
CMDB Confidence Score =
(Highest - Lowest count) / Average * 100
In our example above, CMDB confidence score equals 14. The lower the score, the better.
The real nerdery begins when comparing how many overlapping devices we have in these inventories. It’s possible (but unlikely) that the true number is 534+482+523+512+554, because each inventory lists unique devices.
Using the confidence score
Looking at one CMDB confidence score in isolation doesn’t immediately tell us a lot. The process of calculating the score is probably helpful in itself. Still, the real value comes when you do it systematically, as it indicates the validity of your categories relative to each other.
For example, suppose your CMDB confidence score for Windows servers is 14. Your score for network devices is 23, and your Linux server score is 284.
These numbers clearly tell you that you have a problem with your Linux inventory, while the others are relatively fine.
Many customers begin vulnerability status meetings by reviewing their CMDB confidence scores for the various categories – that never fails to generate interesting discussions.
Another thing that is often worthwhile is comparing the cyber security inventory with the “truth” of each team.
We once met a very confident Linux team at a client site, who were convinced they were patching EVERYTHING running Linux. Yet we quickly discovered more than 150 Linux devices they had never heard of and consequently had never seen a patch.
Granted, some of these were videoconferencing units that intuitively may not register as a Linux device – but the bottom line remains the same: lots of very vulnerable devices that nobody knew existed.
We hope this has inspired you to ways of working with inventories in your cybersecurity efforts. Inventories are the key to taking your cyber security efforts to the next level – not just when it comes to vulnerability management, but everything security.