You may find this cryptic QID in your Qualys scan reports.
But what does it mean, and should you do something about it?
When performing a vulnerability scan, it is important to ensure that the scanner is placed and configured according to vendor recommendations to avoid any potential issues that may arise from scanning true firewalls and routers.
Qualys and other vendors recommend placing vulnerability scanners as close to endpoints as possible, as this can impact the performance of network devices and affect scan results. However, in the real world, it is not always technically possible or economically feasible to follow this recommendation.
If you find QID 34011 in your scan report, it can be useful to understand what it really means and how it affects the vulnerability scan. Essentially, this QID is indicating that the scanner has detected a firewall on the network and is alerting you to the fact that the firewall may be impacting the scan results.

If a firewall blocks a specific port, any attempts to connect to that port will be denied.
This can lead to the client receiving an error message such as an RST (reset) packet for TCP or an ICMP (Internet Control Message Protocol) "destination unreachable" message for UDP.
TCP uses a process called a three-way handshake to establish a connection. In this process, the scanner sends a SYN message to the asset, indicating that it wants to establish a connection.
The asset then responds with a SYN-ACK message, acknowledging the request and indicating that it is ready to establish a connection. Finally, the sender responds with an ACK message, completing the handshake.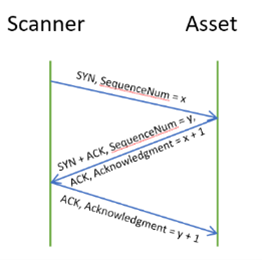
In general, it is not possible to connect to a port that is blocked by a firewall from the “outside”.
This can make it difficult to conduct vulnerability assessments on the endpoint if the port is open and there is a potentially vulnerable service that listens on it and can be exploited. If you are using an "assumed breach model" for your operations, you will likely have knowledge of which ports each endpoint is listening on.
When the firewall blocks all ports except 80 and 443 are filtered as we can see in NMAP and in Wireshark we can see that Qualys Scanner sending SYN packets but not receiving answers from the asset:
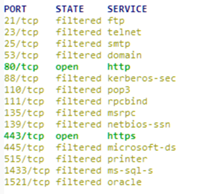
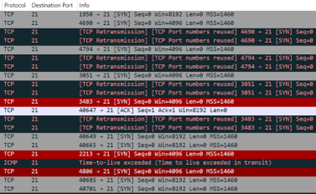
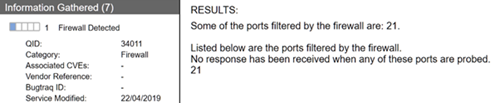
In this case, the scan report will flag all ports except 80 and 443 in Firewall detected section.
A firewall can affect a vulnerability scan by making certain ports appear closed or filtered when they are actually open.
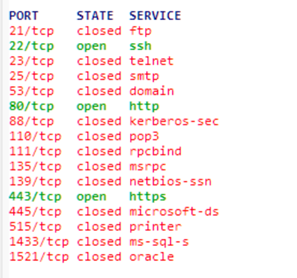
When using a network security tool like Nmap, it is possible to scan a target host and determine which ports are open, closed, or filtered. A closed port is one that is not listening for incoming connections, while a filtered port is one that is not open but also does not respond to connection requests in the same way as a closed port.
To illustrate the difference between “Block” and “Reject” we have set up firewall rules the following way: port 21 “Block” - packets dropped silently, without answer and port 23 “Reject” - RST packets return to the sender.
In NMAP it looks like this:
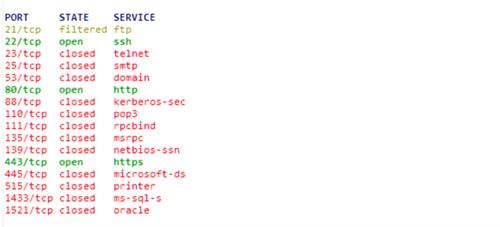
Qualys scan report shows that port 21 filtered by firewall:
When scanner added to “Allow list” on firewall and asset, we don’t see filtered port anymore:
The asset is acknowledging scanner data was sent in SYN in the sequence with an ACK and then notifies the sender that the connection has closed with the RST. In Wireshark it’s looks the following way:

Port 22 is open:
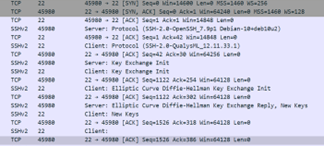
The vulnerability scan report will not include QID: 34011 Firewall Detected for this asset.
For scanning troubleshooting purposes PCAP scan is available in Qualys Cloud Platform for scanner appliances deployed on-premise.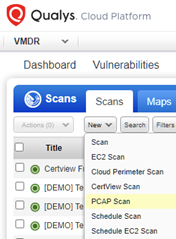
You can also create a widget with a counter of devices behind the firewall, which can be helpful in modern infrastructure where it can be difficult to keep track of all changes:

Vulnerability Query for widget: vulnerabilities.vulnerability.qid:34011
If you see QID 34011 in your scan report, it is important to understand that it is an indication that a firewall is present on the path from a scanner appliance to an asset.
This can affect the scan results and make certain ports appear closed or filtered when they are actually open and reduce the number of vulnerabilities that can be detected by scanning.
It is essential to consider the impact of firewalls and take appropriate actions, if possible, to have an accurate vulnerability assessment and avoid operational disruption.